Installation and Configuration
Supported platforms and downloads
The POS client software runs on Windows, Android, Linux and MacOS. Standard installation packages are available for Windows and Android. Please get in contact, if you want to use Snabble von Linux or Mac. All operation modes (POS, SCO and mobilePOS) are supported by the same software and therefore share the same installer packages.
Installer files can be obtained from the Snabble Retailer Portal, or the Portal for Staging.
| Please find the POS-Release in the menu on the left. | |
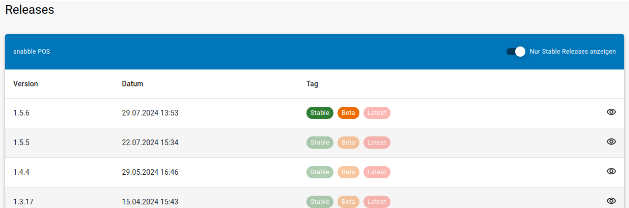 | An overview of releases is shown.You should take the most recent stable version in most cases. |
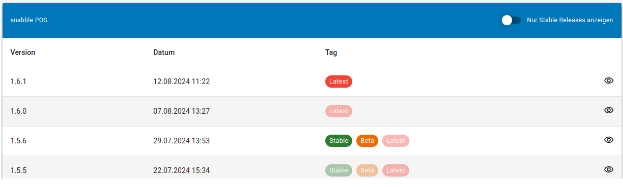 | With the toggle button, also releases from our latest and beta channel are shown. |
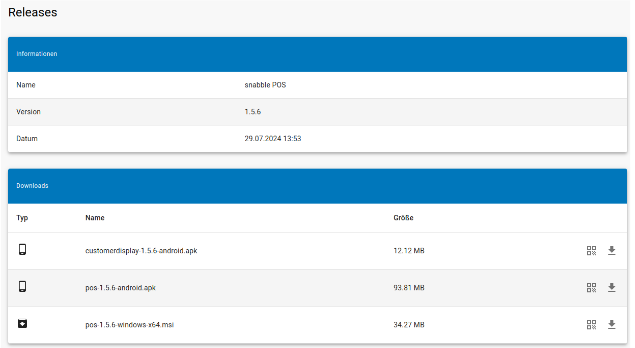 | Select a specific release to see the installer package downloads. |
For a detailed list of supported hardware see the page Hardware Support
Installation
Windows Installation
To install the Snabble POS software on a Windows based computer, simply download the installer file pos-*-windows-x64.msi and execute it on the machine. For full support, Windows 10 Enterprise is required. The software can be executed on other Windows versions, but kiosk mode and auto update mechanisms are only supported on Windows 10 Enterprise.
 | Simple installer package for Windows. |
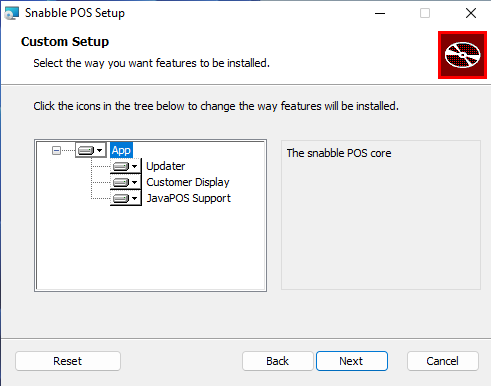 | Please select the components to install.As optional components, there are:
|
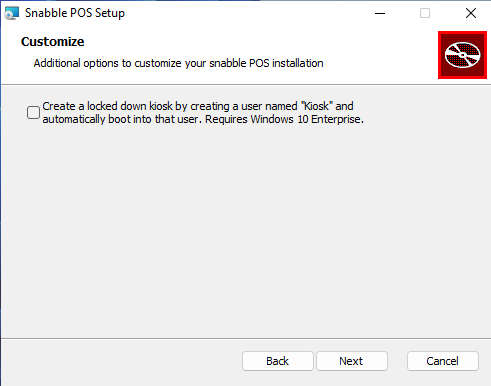 | The recommended installation method for the Self Checkout is using the kiosk mode. This requires Windows 10 Enterprise. |
Windows auto updater service
If you selected the Windows updater service during the installation, the POS software will be updated automatically, as soon as a new release is available. Per default updates will be done for all new stable releases. You can change this the release channel to beta or latest releases in the device configuration within the retailer portal.
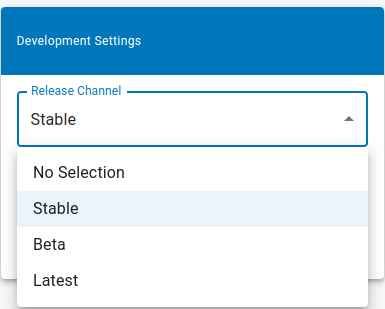 | Select the release channel in the retailer portal. |
Android Installation
In addition to the retailer portal, the most recent stable version for Android is available over the Google Play Store:
| https://play.google.com/store/apps/details?id=io.snabble.pos |
At least Android 7.0 is required. Simply install the APK from the Retailer Portal or Google Play store. If you plan to use the POS mode with customer display, please also install the customerdisplay-*-android.apk, which is only available in the Retailer Portal.
As long as you don’t use a mobile device management software, we recommend using the Play Store to get automatic updates in a convenient way.
Initialization of a POS installation
If you start the POS application right after installation you will see one of the screens above, asking for a configuration. A configuration associates the local installation with a device in the snabble backend. It contains the merchant, store and pos numer. Depending on your device, the configuration can be provided by choosing a config file or by scanning a QR code containing the config.
| On mobile phones and handheld devices the configuration can be scanned by camera or build in scanner. |  |
| On other POS devices, the configuration can be read from a file or by scanning the QR code with a attached scanner. | 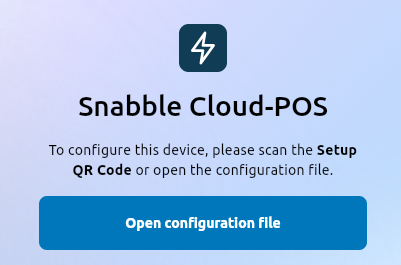 |
Reset a POS installation
If you want to reset a POS installation, you have to remove the configuration. This can be done in the 'Device' section of the config menu of the POS application.
This is for example useful if you want to use the same hardware in a different store.
Device administration
Device creation in Retailer Portal
Before you use a POS device, you have to create the virtual device configuration in the Retailer Portal.
| Navigate to Devices -> Device List . | |
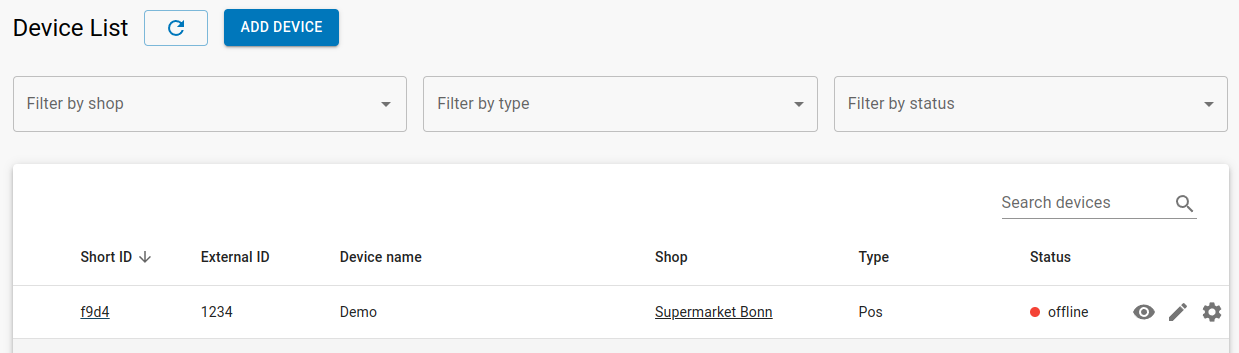 | You see a list with all devices for the merchant. A New device can be added with ADD DEVICE. |
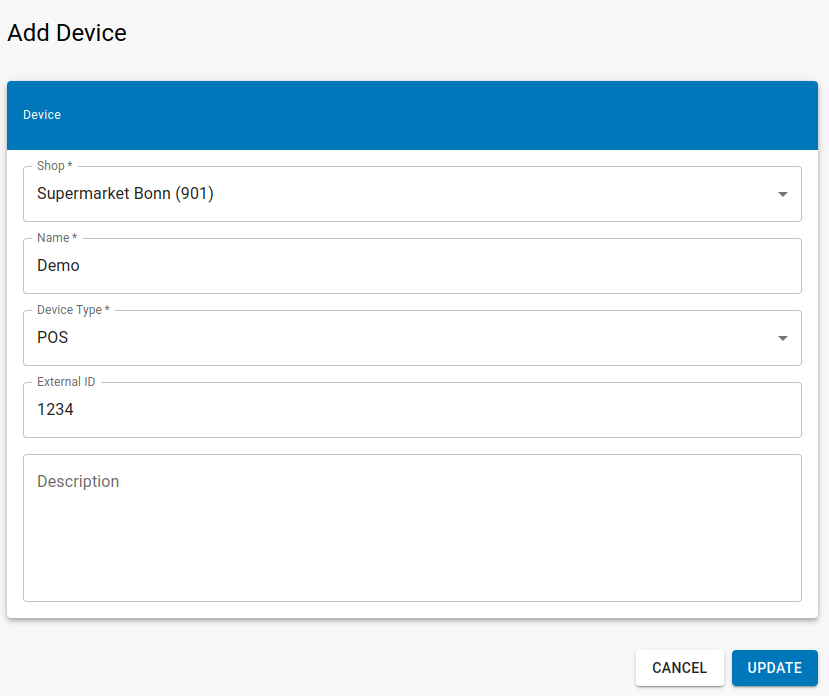 | Select a Store and type in any name which is meaningfull for you.Dependant on you use case select POS or SCO as device type.The External ID is your POS id, which will be refrenced in all exports and reportings. |
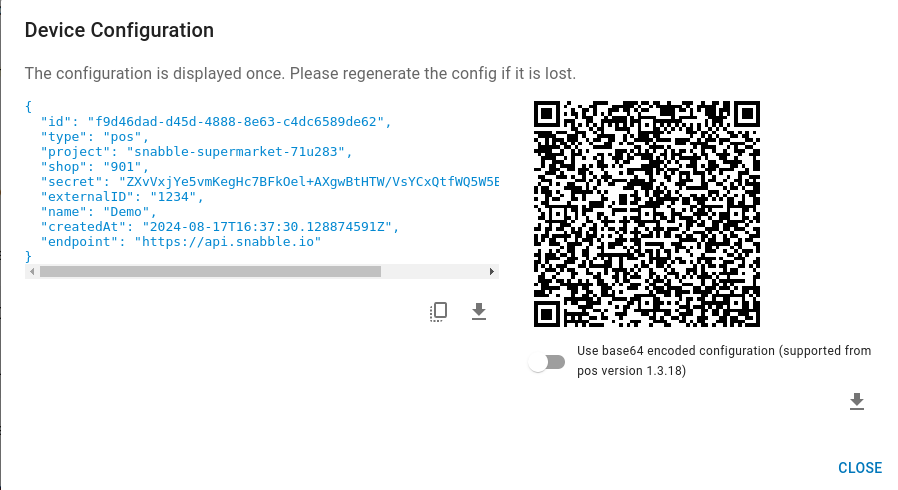 | After device creation, the device configuration is displayed for download. You can download it as file or as QR code and use it for initialisation, as shown in the next paragraph. The configuration is only shown once! If you don't save it, you have to reset the device secret afterwards, which will invalidate an old configuratoin. |
Device Configuration in Retailer Portal
The configuration options of a device can set on different levels: A global level and a configuration for an individual device.
| Access the global device configuration options. | |
 | Access the individual device configuration options in the device list. |
Local configuration menu
The inidividual configuration of a device can also be accessed in the local config menu of the POS or SCO.
Operating System Configuration for Weighing Systems under WELMEC 7.2
The Snabble POS system can be used in combination with a certified weighing instrument in EU countries. The Snabble POS software is delivered without an operating system. Integrators or end users must ensure that the target Windows environment is configured as described above before putting the system into legally regulated use. For legal compliance, particularly for software classified under Risk Class C, the requirements from WELMEC 7.2, including Extension O (General Purpose Operating Systems), must be followed. This section outlines the operating system requirements and provides concrete configuration guidelines for Windows-based installations.
Relevant WELMEC Guidelines
This documentation specifically addresses the following parts of WELMEC 7.2 Extension O:
- O1: Hardware protection
- O3: System resources
- O4: Protection during use
- O5: Protective interfaces
- O6: Identification of the operating system and its configuration
- O7: Protection of the operating system
General Requirements
To ensure the integrity of the legally relevant software, the operating system must be configured in such a way that it:
- Prevents unauthorized access or tampering
- Protects memory and processes from interference
- Allows the legally relevant application to run reliably and securely
- Can be identified and verified during audits
Concrete Windows Configuration Guidelines
✅ O1: Hardware Protection
- Disable all unused hardware interfaces (e.g., serial, parallel, Bluetooth, infrared) via BIOS/UEFI or Device Manager.
- If interfaces cannot be disabled, they must be:
- Physically sealed (e.g., using tamper-evident stickers), or
- Protected by the OS (e.g., restricted access via Group Policy)
- Any interface capable of Direct Memory Access (DMA) (e.g., Thunderbolt, FireWire) must be disabled or sealed.
✅ O3: System Resources
- Ensure at least 2 GB of free RAM are available for the POS and weighing components.
- Disable or limit background services and startup applications.
- Disable power-saving features (e.g., hybrid sleep, hibernation) that may interfere with POS operation.
✅ O4: Protection During Use
- Enable User Account Control (UAC) at the highest level.
- Configure the system with at least two accounts:
- One Administrator account for system configuration only.
- One Restricted User account for POS operation.
- The POS must only run under the restricted account.
- Disable or restrict access to:
- Command line tools (e.g.,
cmd.exe,powershell.exe) - Registry editors
- Control panel and settings app (via Group Policy)
- Command line tools (e.g.,
- Enable BitLocker or equivalent full disk encryption.
✅ O5: Protective Interfaces
- Disable or block unused network ports and services (e.g., file sharing, RDP).
- Use the built-in Windows Defender Firewall to restrict all unnecessary inbound/outbound traffic.
- Block USB storage devices using Group Policy:
Computer Configuration > Administrative Templates > System > Removable Storage Access
- Ensure no third-party applications or services can interfere with the POS or weighing modules.
✅ O6: OS Identification
- The OS version must be clearly identifiable:
- Via the “About” system settings screen
- Or using CLI commands:
winver,systeminfo
- Document the exact Windows build version and patch level for each system during rollout.
✅ O7: Protection Against Modifications
- Apply Windows security and OS updates regularly.
- Protect critical configuration using Group Policy Objects (GPOs) with administrative access only.
- Ensure digital signatures of POS binaries are validated
- Disable access to registry and local security policy tools for non-admins.
Runtime Enforcement (U6)
To detect tampering at runtime, the POS system performs periodic self-verification every 5 minutes. This includes:
- Recalculating the hash of the main binary (
app.so) - Verifying the decrypted embedded source-hash
- Blocking execution and logging an alert in case of mismatch
- The legally relevant software is not altered
- Runtime integrity is continuously monitored
- Any modification attempt is immediately detectable
✅ Summary: Windows Setup Checklist
| Requirement | Configuration |
|---|---|
| Disable unused interfaces | BIOS/UEFI, Device Manager |
| Disable DMA-capable ports | Via BIOS or hardware seal |
| Separate admin/user accounts | Enforced via Group Policy |
| Ensure ≥ 2 GB RAM for POS | Reduce background processes, check available memory |
| Restrict user access | Block CLI tools, registry, settings |
| Full disk encryption | Enable BitLocker |
| Runtime integrity checks | Verify binary + source hash every 5 minutes |
| Network restrictions | Enable Windows Firewall, disable unused services |
| Block USB storage | Group Policy setting |
| OS version traceability | Document Windows build and patch level |